Understanding and Protecting Against the Telegram Scams
August 20, 2024
Overview of the Telekopye Scam:
Emergence and Operation of the Telekopye
The “Telekopye Scam” represents a growing cybersecurity concern in the digital world. This scam involves a malicious “Telegram” bot developed and controlled by a hacker group known as the “Neanderthals”. This Telegram bot leverages phishing websites, phishing emails, and even phishing SMS messages to attack its victims. The Neanderthals have even established an organized hierarchy within their criminal activities by assigning specific roles to its various members.
Telegram Scam Types : This scam includes several different attack methods including:
- Seller Scams: Here, the fraudsters pose as sellers, targeting victims (referred to as Mammoths) by offering non-existent items for sale on Telegram.
- Buyer Scams: In this approach, Telegram users masquerade as buyers, deceiving merchants into divulging their financial details.
- Refund Scams: This nasty tactic involves tricking victims a second time by offering fake refunds on non-existent items.
Telekopye is not a standalone operation; it’s part of a larger scam-as-a-service program called Classiscam. According to research by Group-IB analysts, since its 2019 inception, Classiscam has accumulated more than $64 million in revenue. These scams are meticulously planned, with market research and careful selection of targets based on age, gender, and online marketplace experience.
Sophisticated Tactics:
Transitioning to the techniques employed, the Neanderthals utilize various methods to maintain anonymity, including VPNs, proxies, and TOR browsers. They have also expanded their criminal activities to include real estate scams, creating fake apartment listings in order to dupe victims out of fake reservation fees on fake phishing real estate websites.
The Roles in a Telekopye Phishing Scam: Neanderthals and Mammoths:
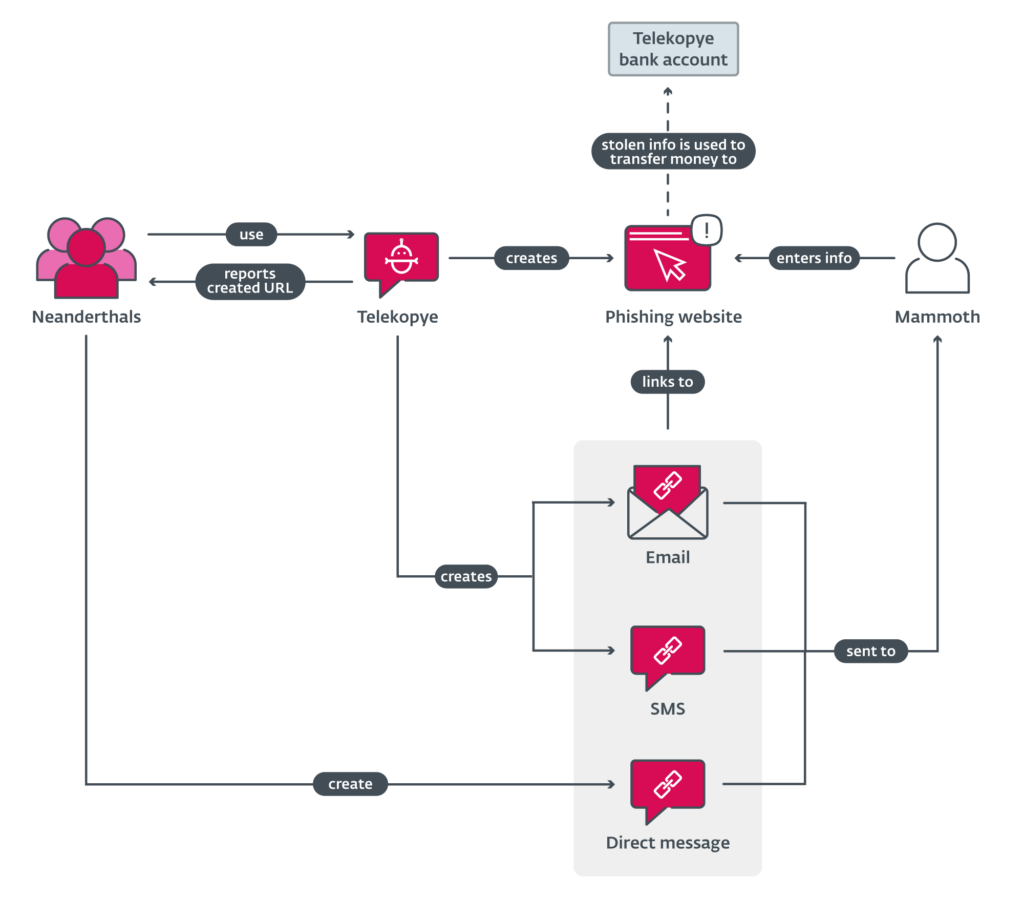
How to Protect Yourself:
TO SAFEGUARD AGAINST SUCH THREATS, CONSIDER THE FOLLOWING STRATEGIES:
1. Be Wary of Unsolicited Offers: Always be cautious of unsolicited seller or buyer offers, especially those that seem too good to be true.
2. Verify the Authenticity: Before engaging in any transaction, verify the authenticity of the website, listing, or individual. Use trusted sources and platforms for online purchases or rentals.
3. Protect Your Personal Information: Never share personal or financial information unless you are certain of the legitimacy of the transaction.
4. Use Secure Payment Methods: Choose only secure and traceable payment methods. Avoid direct transfers to individuals or entities you do not know well.
5. Beware of Phishing Links: Avoid clicking on links sent via email or SMS that ask for personal or financial information. Always verify the source. CyberHoot’s assignment-based phishing can help you identify phish attacks by inspecting various email components (aka: identifiers).
6. Update Your Security Software: Ensure that your devices are protected with the latest security software, and be cautious of any requests to disable these protections.
7. Update Your Software and Hardware: always patch to the latest version of operating systems, applications you use, and update hardware firmware to prevent hackers from breaching your devices and network.
8. Educate Yourself and Others: Stay informed about the latest phishing tactics and share this knowledge with your network to prevent the spread of such scams. CyberHoot’s security awareness training will keep you informed on the latest phish techniques used by malicious actors.
9. Limit what Personal Information you Share Online: the less personal information you share online on social media platforms or publicly, the less hackers can work with to create targeted phishing attacks (aka Spear-phishing) against you.
Conclusion:
Various Telekopye Telegram scams represent a sophisticated and evolving threat. Awareness and vigilance are key to protecting yourself from falling victim. By understanding hacker tactics and exercising caution in online interactions, individuals and businesses can significantly reduce their risk of being targeted and victimized.




